For years, cloud providers have pushed the narrative that "the cloud is secure." And yes, it can be, but only when you put in the work. what most companies discover the hard way is that cloud security is shared responsibility, and the part that fails on you is bigger than you think.
Too many teams assume the cloud magically protects everything. Meanwhile, misconfigurations, overly permissive access, weak monitoring, and blind spots in automation quietly pile up. And in the cloud, small gaps don't stay small, they scale with your infrastructure.
That's where modern cloud security tools actually matter. Not the flashy dashboards, not the buzzwords, the tools that genuinely reduce risk and close the gaps attackers love to exploit.
Let’s break down what’s really putting your cloud at risk today, the tools that solve those problems, and how forward-thinking teams build security that scales.
The Cloud Isn’t Failing — Your Visibility Is
If you look at the root cause of most cloud breaches, you see the same pattern over and over:
“We didn’t know this was exposed.”
“We didn’t realize that permission was still active.”
“We didn’t see the anomaly until it was too late.”
The issue is rarely a lack of power in AWS, Azure, or Google Cloud. The issue is that cloud environments grow and mutate faster than humans can track. A single missed configuration today becomes a breach vector tomorrow.
This is why the smartest companies focus on visibility before anything else.
The Tools That Restore That Visibility
Below are the categories of cloud security tools that matter — the ones that actually eliminate guesswork and expose hidden weaknesses:
- CSPM (Cloud Security Posture Management)
- CWPP (Cloud Workload Protection Platforms)
- IAM Governance Tools
- CIEM (Cloud Infrastructure Entitlement Management)
- SIEM/SOAR Platforms
Most companies start adopting these tools only after an incident. The wiser ones start long before.
The Hidden Gaps You Don’t See (Yet)
Every cloud setup has weak points — even the “well-managed” ones. What makes cloud risk so dangerous is that gaps rarely show themselves until an attacker abuses them.
Here are the ones that quietly cause the biggest problems:
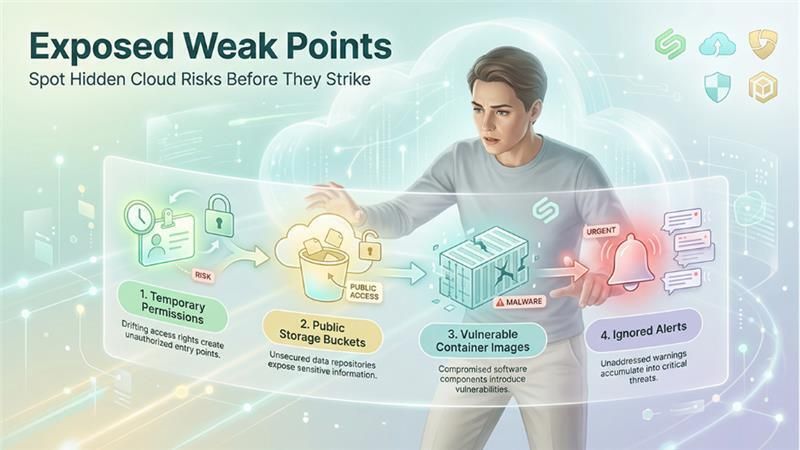
1.The “Temporary” Permission That Never Gets Removed
A developer gets admin access for a five-minute hotfix.
Months later, the role still exists — and now it’s a gift-wrapped privilege escalation path.
Best tool to prevent this: IAM governance + CIEM tools that track permission drift.
2. The Storage Bucket That Was Public and “Didn’t Matter”
You think it only contains harmless assets.
Then someone uploads sensitive logs by mistake.
Now that public bucket becomes a liability.
Best tool: CSPM platforms that continuously check exposure levels.
3. The Container Image With a Vulnerability You Forgot About
Containers are treated like black boxes. Teams assume if the cluster is secure, the app is secure.
Wrong.
One outdated image can open the door.
Best tool: CWPP platforms that monitor containers in real time.
4. The Alert You Ignored Last Week
Security teams drown in alerts. Attackers know this.
A single ignored anomaly — an unusual token, a suspicious login from a new region — can turn into a breach.
Best tool: SIEM/SOAR with automation and context-driven alerts.
Why Cloud Security Fails: The Pace Problem
Traditional security falls apart in the cloud because the cloud moves faster than any checklist.
Infrastructure changes hourly. Servers spin up and vanish. Developers deploy constantly. Data flows everywhere. And the attack surface expands with every new service you adopt.
Static security can’t survive in a dynamic environment.
This is why the next generation of cloud security tools focuses on three things:
1. Automation
“No human can remediate misconfigurations at cloud speed.”
The best tools don’t just alert you — they fix issues instantly or open tickets automatically.
2. Context
Modern security isn't about having more alerts. It’s about knowing which one matters right now.
3. Continuous Evaluation
No once-a-year security audit can keep up with an environment that changes every five minutes.
Today’s cloud security strategy is continuous, not periodic.
How Smart Teams Build Real Cloud Security in 2025
The companies that stay ahead don’t rely on luck. They build a layered defense that assumes breaches will happen, and minimizes the damage if they do.
Here’s what that approach looks like:
1. Identity is the first perimeter
IAM tools define who can access what. Get this wrong and nothing else matters.
2. Misconfigurations get treated as incidents
Because in the cloud, they are.
3. Workloads get protected like the crown jewels
Clusters, containers, functions — everything running in production stays monitored and hardened.
4. Monitoring becomes real-time, not reactive
SIEM + SOAR turns detection into response instead of dashboards into decoration.
5. Automation handles the boring but critical tasks
Drift correction, patching, compliance checks — all of it happens before humans wake up.
Your Cloud Won’t Get Safer on Its Own
Cloud security doesn’t become stronger just because you hope it will. And it doesn’t improve because you bought another license or read another vendor pitch.
It improves when you build real visibility, apply identity discipline, protect workloads intelligently, and automate the work humans can’t keep up with.
Modern cloud security tools aren’t about checking boxes — they’re about eliminating gaps that attackers would otherwise exploit long before you notice.
The companies that thrive in the next decade will be the ones that treat cloud security as a dynamic system, not a static setup.
If your cloud keeps growing, so should your defenses.




Top comments (0)